Having too many things to do and not knowing where to start is a common struggle we’ve all faced. This feeling is easily applicable to Splunk. Whether you’re beginning in a brand-new environment or working out of an established one, it’s easy to be overwhelmed—especially when it comes to detections.
Regardless of environment, the variety of detections that can be written and enabled will often leave you with this feeling of not knowing where to start. Splunk Enterprise Security Essentials offers 1,800+ detections across Enterprise Security, ES Content Updates, UBA, and the ES app itself. Understanding your options, having a clear plan for your Splunk detections, and strategically selecting where to spend your time is the key to getting the most value out of your detections.
Keep reading for a quick guide on strategizing, planning, and simplifying your Splunk detections.
Where to Start with Splunk Detections Planning
The first thing to address is what can be done to start the planning and strategizing process. There are a lot of detections out there that may be focused on one specific cloud provider, SaaS vendor, type of endpoint or log source, and if this is not applicable to you, then let’s start by removing the noise.
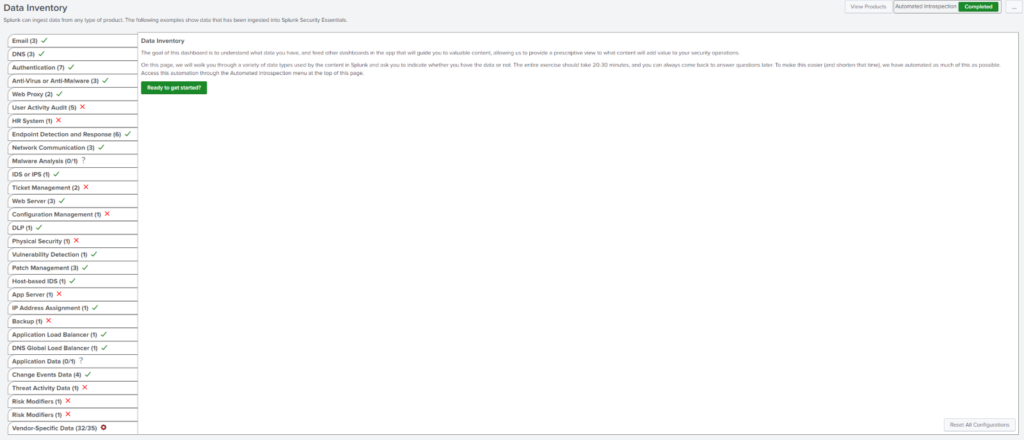
Splunk Security Essentials’ Data Inventory allows you to inventory your data sources and note what you do and don’t have across different data sources. Splunk then works to display content that is available based on your data. While going through this process and building a road map, it’s important to keep an eye on what data sources may be upcoming or what you may have not been able to onboard into Splunk yet based on constraints. While it’s not pressing to focus on these items now, you don’t want to leave them out for the future.
Targeting Threat Groups’ TTPs
After dwindling down content based on what is available to you, you’ll still likely have a list of hundreds of detections. The next thing to consider is: who is likely to attack? MITRE has great resources for threat groups and the types of industries these threat groups typically target. Attackers may target organizations based on geographic locations, the type of industry they are in, or their ultimate goals.
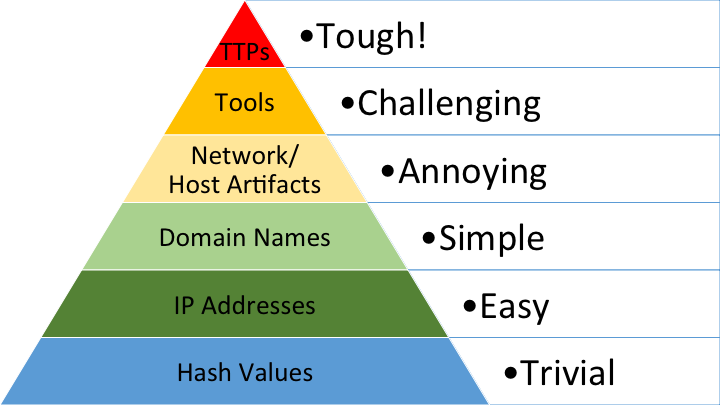
While specifically targeting certain threat groups may seem like it could leave gaps, it is important to note that many groups share common TTPs (Tactics, Techniques, and Procedures). Covering for one group will also provide coverage for other groups that share similar TTPs. It is important to focus on these when reviewing something like the Pyramid of Pain, as TTPs are commonly the most difficult thing for attackers to adapt in their approach. Hashes, IPs, Domain Names, etc., can be changed with ease, but the actual techniques that groups tend to use cannot be updated so simply.
Increasing the Value of Splunk Detections by Minimizing Gaps
Staying on the topic of MITRE’s ATT&CK Framework and working with TTPs, the next step to focusing your detection efforts is to determine where your gaps are. Finding gaps and remediating those directly results in getting more value out of your detections. Whether gaps come from previous incidents, red teaming exercises, risk assessments, or automated attack simulations—you’ll begin to know what you cover well or what you don’t cover well.
Maybe you have an amazing EDR product handling malware detections and know you have some risk with websites you are hosting—rather than focusing on some of the detections such as a malware outbreak, you focus your attention on WAF, SQL, and web logs to find attacks being attempted. You might also have had red teaming exercises in the past where a tactic such as Exfiltration was commonly detected by your other security controls, but Lateral Movement in the network went undetected, so you want to put your focus within that tactic.
While these are some basic examples, it’s good to bring attention to the value of having defense in depth as well. However, if you know you lack the ability to detect specific techniques currently, it would be good to focus on those higher risks first.

Building a Splunk Detections Roadmap
Once you’ve defined the areas you’d like to focus on, Splunk Security Essential’s Analytics Advisor allows you to select the threat groups, tactics, and techniques before displaying content that is relevant/available to you based on your log sources. There are other filters that can be used to define this such as specific data sources.
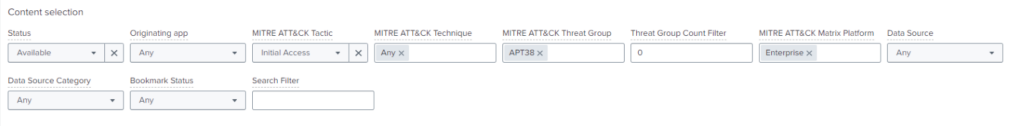
You can then bookmark these detections and manage the detection lifecycle through the “Manage Bookmarks” page. This allows you to track if the detection is waiting on data, tuning, ready for deployment, or has been successfully implemented. As you go through the process, the “Analytics Advisor” tracks what you have marked as implemented and will build a copy of the MITRE ATT&CK Framework highlighting what is and isn’t covered. Taking this approach can be used to help plan the next round of detections by highlighting your gaps.
Summary
Ultimately, there are a lot of useful detections out there. However, knowing which ones to put time into setting up, tuning, and responding to will give you the most value in the shortest amount of time. Focusing on detections that are relevant to you based on data sources, figuring out who is most likely to attack you, identifying where your gaps are, and planning to cover those gaps, will give you the most efficient route to having a good detection strategy.
SP6 Consulting offers Security Use Case Workshops and Managed Services to help organizations through the process of planning detection road maps, building out detections, and tuning detections. Get in touch with us to see how we can help get the most value out of your Splunk investment and bolster your detections for maximum efficacy.
