At SP6, we understand the critical importance of proactive cybersecurity measures, which is why we offer the Security Use Case Development Workshop—a tailored program designed to empower organizations with the right path toward their highest security maturity journey.
In today’s digital landscape, where cyber threats continue to evolve in sophistication and frequency, organizations are under increasing pressure to fortify their defenses and protect sensitive data. With many years of experience working with hundreds of valued clients, we have observed that most of the organizations leveraging SIEM to manage their detections and monitoring have been using general OTB, site-specific, or highly customized use cases.
The primary goal of our Security Use Case Development Workshop is to create a comprehensive roadmap and prioritize use cases that align with the MITRE ATT&CK framework. This framework, renowned for its depth and relevance in illustrating adversary tactics, techniques, and procedures (TTPs), serves as the cornerstone for developing robust cybersecurity strategies.
What sets SP6’s workshop apart is our commitment to providing an elite service and experience that enables organizations to build their detections, responses, and monitoring objectives efficiently and effectively by leveraging the best practices outlined by MITRE ATT&CK Framework and Splunk’s content library that consists of more than 1,500 use cases.
Security Use Case Development Workshop Methodology: Getting the Best Value Out of Your SIEM Solution
SP6 consultants conduct Security Use Case Development Workshops with solid process and time management ensuring that all required documentation will be discussed and delivered to your organization and stakeholders. Here is the high-level process of SP6’s Security Use Case Development Workshop:
- On the first day, our consultants will conduct intensive questionnaire sessions to collect valuable information about your security operations center (SOC). This will drive the content for the final UCDW deliverable. A sample of questions may include:
- What is your primary mission? Are you trying to solve the insider threat? Corporate Security monitoring? OT security? Supply Chain? Something else?
- Identify some of your short-term and long-term monitoring goals.
- What are some of your biggest risks and threats to the organization? What keeps you up at night?
- Once all the answers have been collected and documented, consultants will dive into your organization’s environment and conduct a technical discovery. This process will identify the data sources and enrichments relevant to your security posture.
- Then, consultants will build the initial use case recommendations draft aligning with your visions and challenges. This draft should be aligned with best practices mapped with the MITRE ATT&CK framework.
- After this, consultants will be conducting sessions to identify gaps in data sources, note irrelevant use cases, and prioritize applicable use cases depending on three main factors:
- Business risk (BR) scored from [0-5] with 5 as critical.
- Organizational difficulty (OD) [0-7] with 7 as the hardest to overcome.
- Technical challenges (TC) scored from [0-5] with 5 as the hardest to implement.
- With discovery sessions completed, our consultants will work on building the final documentation for the workshop which will consist of the following:
- A roadmap document that summarizes all the efforts and results driving the Security Use Case Development Workshop.
- A sheet of final use cases inventory that is prioritized and categorized, along with data sources and enrichment analysis and recommendations.
- A custom dashboard that will visualize the use case categories and MITRE ATT&CK coverage.
- All these deliverables will be shared and discussed with you during the workshop. This is so you’re aware of the return-on-investment (ROI) value of this workshop.
Why MITRE ATT&CK? Understanding the Foundation of Effective Cybersecurity
In cybersecurity, staying ahead of adversaries requires a comprehensive understanding of their tactics, techniques, and procedures (TTPs). This is where the MITRE ATT&CK framework plays a pivotal role. Developed by the MITRE Corporation, a renowned non-profit organization dedicated to advancing technology for public interest, the MITRE ATT&CK framework provides a structured and comprehensive model for characterizing and categorizing adversary behaviors.
Here are key reasons why the MITRE ATT&CK framework is indispensable in the context of cybersecurity and the Security Use Case Development Workshop:
- Real-World Relevance: The MITRE ATT&CK framework is grounded in real-world observations of cyber threats. It catalogs a wide range of adversary tactics and techniques based on extensive research and analysis of actual cyber incidents. This real-world relevance ensures that organizations can align their security strategies with tangible threat scenarios.
- Granular Visibility: One of the strengths of the MITRE ATT&CK framework lies in its granular visibility into adversary behaviors. It breaks down attack techniques into discrete tactics, providing detailed insights into how adversaries operate across various stages of the cyber kill chain. This level of granularity is instrumental in developing precise and effective use cases for threat detection and response.
- Standardized Framework: By providing a standardized framework for describing cyber adversary behavior, MITRE ATT&CK facilitates communication and collaboration within the cybersecurity community. It allows organizations, security vendors, and researchers to speak a common language when discussing threat intelligence, attack patterns, and defensive strategies.
- Threat-Informed Defense: Leveraging the MITRE ATT&CK framework enables organizations to adopt a threat-informed defense approach. Rather than relying solely on generic security measures, such as signature-based detection, organizations can proactively identify and mitigate threats based on known adversary behaviors. This proactive stance is essential in mitigating advanced and targeted attacks.
- Continuous Improvement: The MITRE ATT&CK framework is continuously updated and expanded to reflect emerging threats and evolving adversary tactics. This dynamic nature ensures that organizations can stay current with the latest cyber threats and adjust their security strategies accordingly. It also encourages a culture of continuous improvement and adaptation in cybersecurity practices.
How Does the Security Use Case Development Workshop Leverage the MITRE ATT&CK Framework?
In the context of the Security Use Case Development Workshop, the MITRE ATT&CK framework serves as a foundational element for creating targeted and effective security use cases. By mapping industry-specific risks to the MITRE ATT&CK framework, organizations can enhance their threat detection capabilities, streamline incident response processes, and fortify their overall cyber resilience.
This workshop, coupled with our ongoing efforts, will ensure the development of a meticulously curated list of use cases tailored to your organization’s unique environment. As a result, we anticipate achieving a significant 25-35% coverage of MITRE techniques, out of the total 84% options available in Splunk.
It’s important to note that many companies that overlook a security use case workshop often fail to align with industry standards. This makes it challenging to accurately measure security maturity growth over time. In contrast, companies that engage in such workshops typically aim for an average coverage percentage of 5% to 10%—this is driven more by intention than mere chance. Here is a real example that visualizes the coverage for one workshop we recently completed:
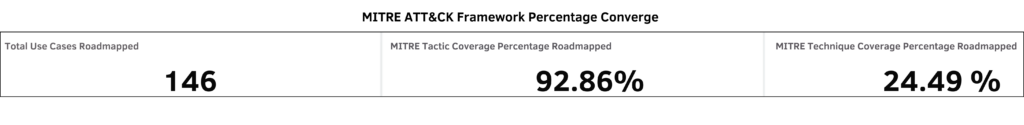
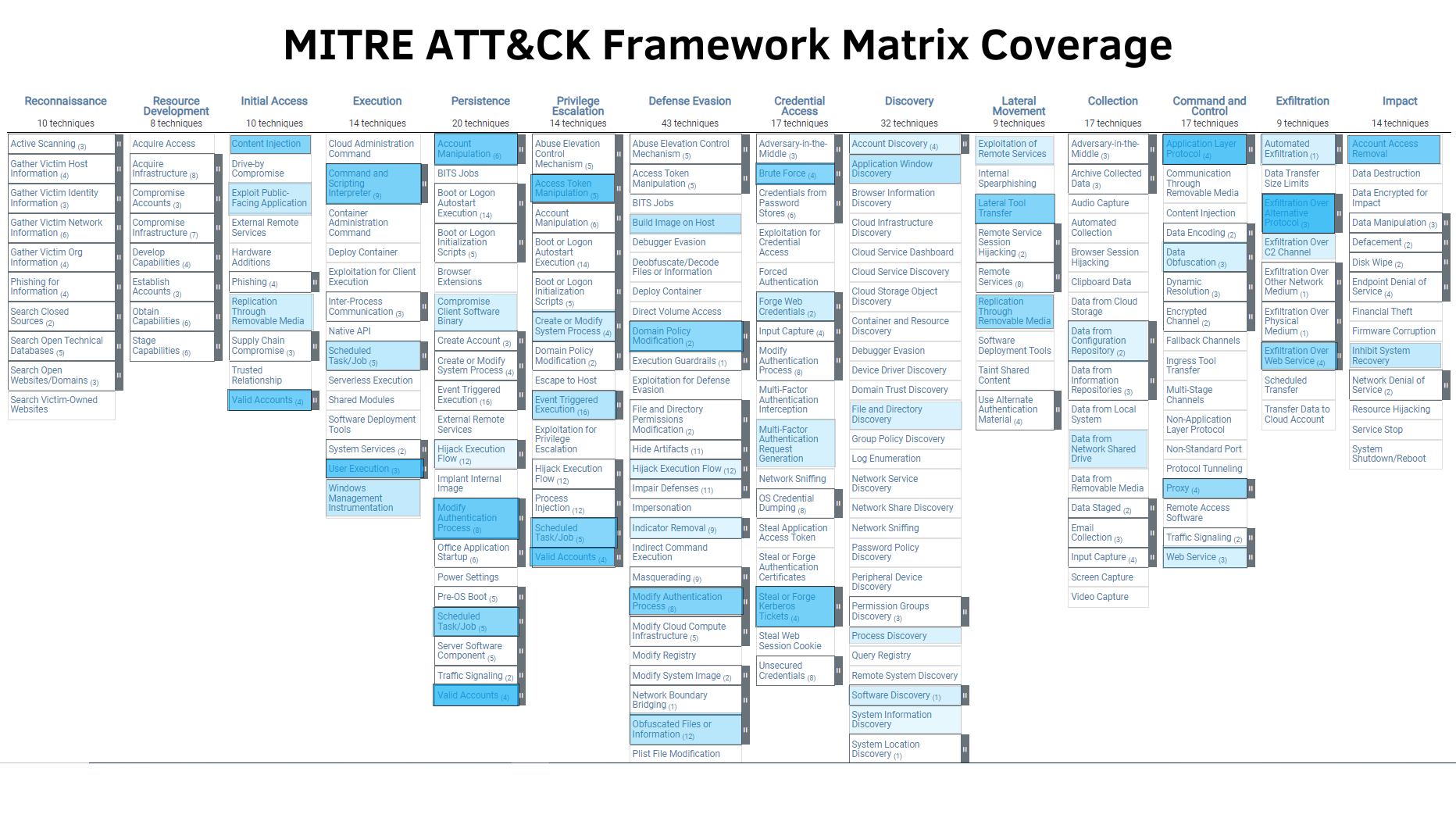
Delivery: How SP6 Produces Valuable Results
- Expert Guidance: Our team of certified cybersecurity consultants brings a wealth of experience and expertise in leveraging Splunk technology and the MITRE ATT&CK framework. They’re prepared to guide you through every step, ensuring a thorough understanding of industry-specific threats and tailored use case development. By prioritizing consistent support during the workshop, our team is able to work with yours, discovering challenges, the scope of interest, your current environment and resources, and your incident response team’s short and long-term goals.
- Customized Approach: We recognize that each organization faces unique challenges and threat landscapes. Therefore, our workshop takes a customized approach, focusing on mapping your industry-specific risks to the MITRE ATT&CK framework. This ensures that the use cases developed are relevant and impactful. We also help your organization to identify gaps in their data sources that would add more value to your security posture.
- Practical Application: The workshop goes beyond theoretical concepts by emphasizing practical application. This is done by analyzing the current data sources and making sure to identify data CIM issues. We also analyze sources of assets, identities, and threats enrichments. This allows you to engage in hands-on exercises to understand and evaluate each use case’s impact and overcome scores. These scores will lead to setting the priority of each case.
- Road Map for Success: By the end of the workshop, your organization will walk away with a clear road map and prioritized use cases that strengthen your security posture. These actionable insights enable proactive threat hunting, rapid incident detection, and effective response capabilities.
At SP6, we are dedicated to equipping organizations with the knowledge, experience, and strategies needed to stay ahead of evolving cyber threats. Our Security Use Case Development Workshop exemplifies our commitment to delivering tangible results and driving our clients to achieve their best security posture.
